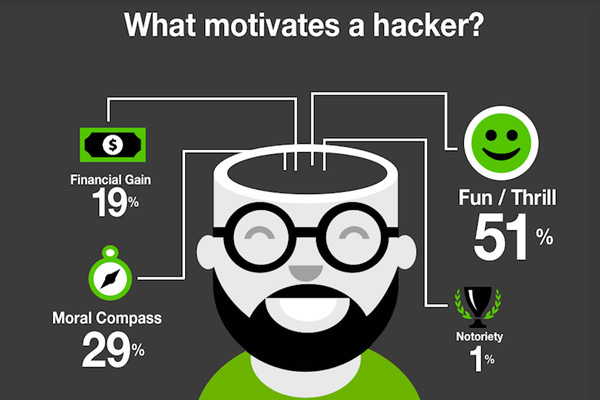
You can rest assured that the cyber crime’s hand is a long one with surprisingly skillful fingers. When it comes to the modern day hackers you simply cannot exaggerate. However, this one is a little bit hard to swallow without the bitterness, even for the most pessimistic IT security pessimists.
We have completely neglected what is happening above our heads. The impressive army of weather satellites flies around carelessly and without the proper cyber defense on the ground. Yes, you heard that one correctly. Potential troubles in the sky may have solid ground origins and causes.
You may ask yourself, who in the world would try to hack the IT infrastructure of the weather satellites? And why? Better think twice. These satellites can come in handy for the spying purposes. You can do some spying and later offer your findings for a nice price. Does this one sound like a good hacker’s plan?
What can we do about it? Well, there is so much to do it. We should begin by paying some additional and absolutely necessary IT security attention in this field. You cannot control both bad weather and bad hackers, but you can certainly predict their actions. IT and weather security are all about proper predictions. Right?