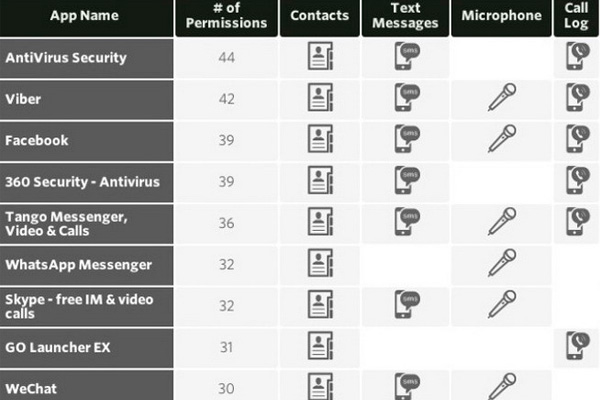
Can you guess which top 10 countries are on the Twitter-withdraw-blacklist? You know how it goes, don’t you? You submit a request to Twitter asking for a certain content to be removed, and then you sit and wait for a response. It is not so hard to guess, who is the number one, is it? Turkey, who else.
Turkey submits more than 500 requests, the official ones, on a yearly level, and Twitter answers in about 50% with a green light. The second position is reserved for Russia, of course. However, when it comes to the Russian, then the blue bird answers positively in less than 10% of all cases. Here is a surprise.
Germany has just won the bronze medal. This is a little bit surprising. Now, the remaining magnificent seven: France, the USA, Brasil, the UK, Japan, Netherland, and India. So, what is the moral of this story? Do not you even dare to come up with some reckless parallels between the democracy and Twitter.
For what is worth, it is definitely not a good sign, when you want to remove something on Twitter. It is worth mentioning that both Russian and Turkish politicians like to use Twitter, especially during the election years. You like when Twitter users vote for you, but you hate it when they criticize. Interesting.