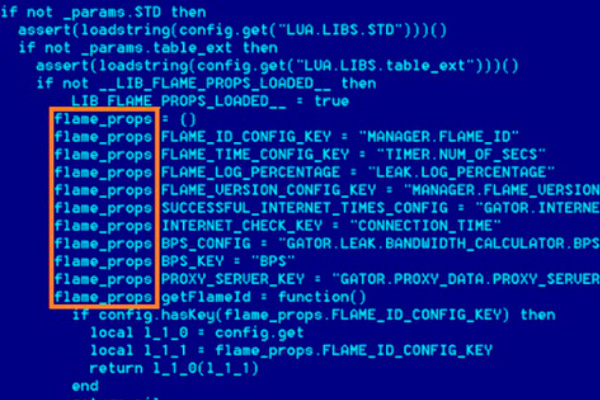
The latest cyber monster, which is after your virtual money, has a name. The Vawtrak malware has begun with its global domination in Japan. So far, the serious estimates say that more than 100,000 computers have been infected. This malicious software follows your online banking transactions.
It has a simple goal. The Vawtrak transfers your money to the third party bank accounts. The users all over Asia have already lost more than hundreds of millions of dollars. Now, when we are fully aware about this financial danger, what can we do in order to eliminate it, for good?
You can rest assured that quite a few busy little bees in the cyber security sector work day and night on an efficient solution. As always, it is a merciless race against the time itself. The Vawtrak is moving from the West toward the East. How much time we have left before the real trouble?
As soon as it hits the cyber shores of Europe and the USA, we will be facing the completely new level of the cyber disaster. One important piece of the cyber puzzle is missing, though. No one told us, how all of those computers got infected in the first place. That is worth knowing. Is not that right?