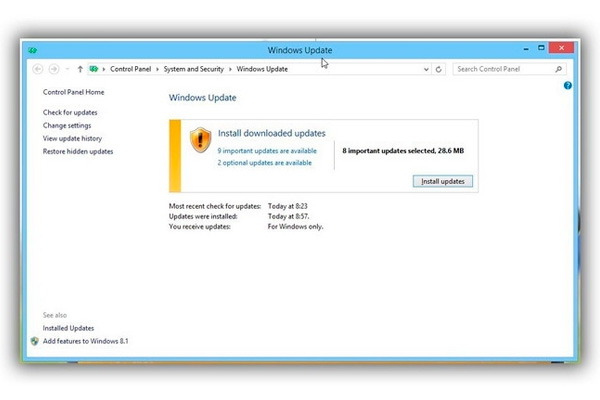
Well, hell, it is about time. Why did we have to wait so long? To tell the absolute truth, we do not have a clue. Yet, for what is worth, Microsoft has closed the security door opened by Google. To be quite honest, Google has not done anything wrong, it just warned about the serious security flaw in Windows 8.
On the other hand, Microsoft was obviously hit straight into its most serious nerve. Microsoft replied that Google worries too much about its competitors, rather and more than its own customers. Then, we had to wait for more than four months to get this security patch in order to have careless dreams.
At the same Google has troubles of its own with the Android 5.0, or better known as the Lollipop. However, it is obviously easier to deal with other people’s problems, than your own, isn’t it? In addition, Microsoft just could not have issued a security patch for a single issue, regardless of its seriousness.
So, what is going to happen now? Are we to expect that Microsoft is to strike back? How? Well, it can find some vulnerability in Google’s system in return. In the meantime, while these two IT giants play their vanity games, we the users, still have to tremble. Does it really have to be this way? For real?